The Role of Cybersecurity Insurance in Risk Management
What is Cybersecurity Insurance?
3 min read
 Lucas Hathaway
:
22 Mar 2024
Lucas Hathaway
:
22 Mar 2024

Originally launched in 2014 and updated in 2018. NIST CSF 2.0 (released in February 2024) builds on ten years of cybersecurity progress. It expands from critical infrastructure to all industry sectors, organization sizes, and cybersecurity expertise levels.
“Developed through close collaboration with stakeholders and incorporating the latest cybersecurity challenges and management strategies, this update aims to enhance the framework's relevance to a broader range of users in both the United States and internationally,” stated Kevin Stine, chief of NIST’s Applied Cybersecurity Division.
Below is an overview of the new framework. It highlights the key updates and changes that financial institutions should note.
You have likely heard the biggest takeaway from NIST CSF 2.0 by now is governance, as it has expanded to play a larger role in their framework. What was once a category has now turned into a core function with its own categories and subcategories.
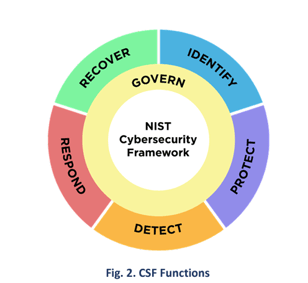
Positioned at the core, the Govern function highlights the importance for organizations to establish and monitor their cybersecurity risk management strategy, expectations, and policies while facilitating discussions on risk communication with executives. It also stresses integrating cybersecurity into risk management. This aligns with recent updates to regulations. For example, the SEC's cybersecurity disclosure rule and the NCUA's 72-hour Incident Response rule.
Also, the Govern function emphasizes supply chain management and the involvement of third parties in an organization's security. It includes a category called Cybersecurity Supply Chain Risk Management (GV.SC).
The framework now provides thorough guidance within the Govern function in creating processes to identify, evaluate, and mitigate risks associated with suppliers and third-party relationships.
There is also an emphasis on managing cybersecurity supply chain risk. This reflects NIST's latest guidance on deploying secure software. These practices include making a Cybersecurity Supply Chain Risk Management (C-SCRM) strategy. They also include objectives, policies, and processes. Additionally, organizations are encouraged to identify their technology suppliers and assess their criticality to the organization, while establishing roles and requirements for C-SCRM and communicating them both internally and externally.
To encourage broader adoption, NIST developed a suite of implementation resources. One way they do this is through the updated reference tool which lets users access, search, and export core guidance data in user-friendly and machine-readable formats.
The new and comprehensive reference tool allows users to efficiently navigate NIST CSF 2.0, enabling them to swiftly locate subcategory references and implementation examples using keywords and phrases. Furthermore, the tool informs users about organizational profiles. It does this by giving examples of mission statements, stakeholder expectations, legal requirements, and rules for contracts.
Another resource is the quick start guides. They aim to help you integrate into your organization's cybersecurity program.
Like CSF 1.1, NIST has given detailed guidance for different entities. These include educational institutions, healthcare organizations, and businesses of all sizes. This ensures that all, regardless of their current cybersecurity level, can use cybersecurity best practices. This means that even organizations with limited resources or expertise can swiftly and effectively reduce their cybersecurity risks.
What were previously two sub-categories (ID.DR-2 and ID.RM-3) has now been consolidated into one sub-category found within the risk management.
This highlights the significance of establishing an appropriate risk tolerance level for effective cybersecurity governance. With a defined risk tolerance level, organizations can make more informed decisions regarding cybersecurity investments and resource allocation. They can prioritize efforts based on the potential impact of a security breach, focusing on areas with the most severe consequences. By talking to our clients, we have found that utilizing a quantitative risk assessment approach is the best way to grasp this severity.
The introduction of the new core function, Govern, in NIST CSF 2.0 suggests that security discussions will overwhelmingly focus on aligning cybersecurity with business strategies. These discussions involve operations leaders who understand the impact of security initiatives on a day-to-day basis alongside security executives (including board members) who can demonstrate how these efforts contribute to broader organizational goals.
Additionally, this new framework places greater emphasis on managing cybersecurity risks within the supply chain. This is vital for financial institutions as they rely heavily on many third-party vendors for services, technology, and critical infrastructure. With NIST 2.0, financial institutions are required to conduct thorough assessments of their supply chain partners, ensuring that adequate cybersecurity measures are in place across the entire ecosystem. This focus on supply chain security aims to reduce the risks from third-party vulnerabilities, unauthorized access, data breaches, and other threats. These threats could harm the integrity, confidentiality, and privacy of sensitive financial data.
With cyber risks on the rise, NIST's latest guidance comes as a much-needed update to a framework widely used across various industries. The real test lies in how well organizations can embrace the new ideas and tools in CSF 2.0 to boost their risk management skills effectively.
By using Rivals Data Security platform, organizations can map the newly released NIST CSF 2.0 framework along with a host of other frameworks (CIS, ISO 27002, ACET, CAT, FedLine, SOC 2, HIPAA, PCI DSS 4.0, and more) in a matter of minutes, enabling security teams to streamline compliance efforts and ensure faster audits using our 1-click artifact download feature.
Schedule a quick demo to learn more about our cybersecurity platform.

What is Cybersecurity Insurance?

For financial institutions, protecting sensitive customer data and meeting regulatory requirements isn’t just critical—it’s non-negotiable. NIST...

As organizations increasingly migrate workloads to cloud infrastructure, securing these environments has become both crucial and complex. Effective...